Impacket Remote Execution Tools: smbexec.py
smbexec.py is a script that comes with Impacket. It allows remote code execution through a semi-interactive shell by creating services that execute commands sent by the attacker. This blog post is a post from a series of posts to analyze Impacket remote execution tools (the previous post was the analysis of the atexec.py). In this blog post we will take a look at how this tool work, analyze it’s artifacts and write Rhaegal rules to automate detection.
Lab Environment
This lab environment does not have any kind of additional monitoring or logging (the default config) to simulate worst case scenario. The following table lists the lab environment specifications:
| Hostname | IP | Operating System | Role |
|---|---|---|---|
| LAB-DC01 | 10.10.10.2 | Microsoft Windows Server 2012 R2 Standard | Domain Controller (lab.com) |
| PC | 10.10.10.138 | Kali | Attacking Machine |
The user used for remote code execution is dcadmin which is a Domain Admin user.
Analysis
You can download Impacket along with smbexec.py from HERE. Let’s start by executing the following command:
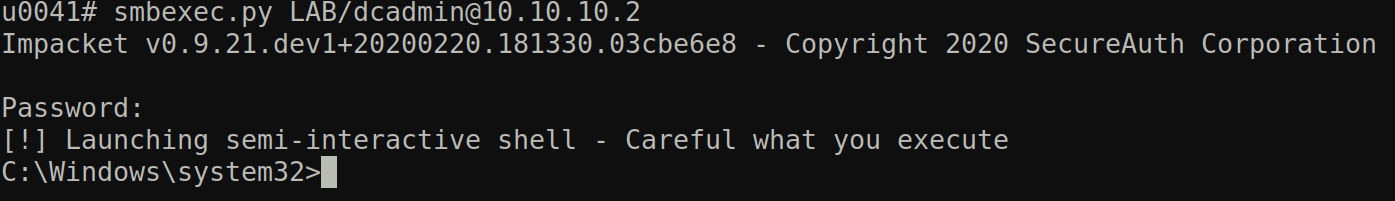
After executing this command a connection will be established with the remote server and three Windows Event Logs will be recorded, The first is successful login (Security Event ID 4624) with the login type 3. The second is a service creation on the System log with the Event ID 7045. Finally an event in the System log with the Event ID 7009. The following is the service creation event in the System log (Event ID 7045):
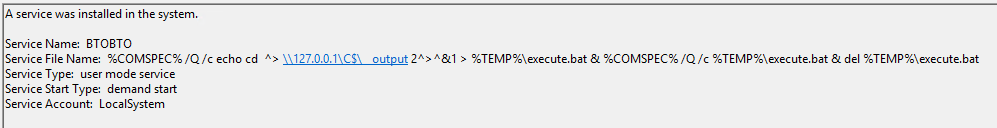
The service name is set to BTOBTO which is a hard coded service name. The Service File Name or the binPath for the service is the command to be executed. The above command will do the following:
- Write the command cd > \\127.0.0.1\C$\__output 2> &1 to the file %TEMP%\execute.bat which is C:\windows\temp\execute.bat because it is running as SYSTEM.
- Execute C:\windows\temp\execute.bat.
- Delete C:\windows\temp\execute.bat.
- Get command results from C:\__output ( same as \\127.0.0.1\C$\__output).
- Delete C:\__output.
When you first connect cd will be executed so it will show up as the current working directory on the semi-interactive shell (C:\windows\system32 in this case). Some time the command will fail before clean up which will result in the file execute.bat and __output not being deleted. In this example I ran the command ping -n 50 127.0.0.1 that crashed smbexec.py with the following error message:
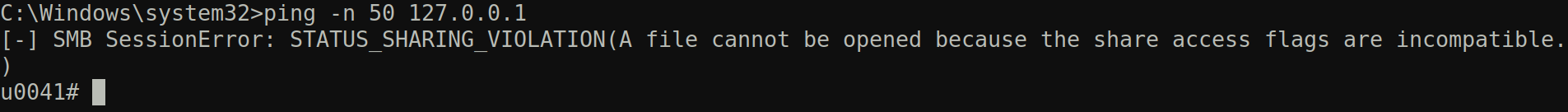
If we go to the server we can see the file execute.bat and __output still on the system:
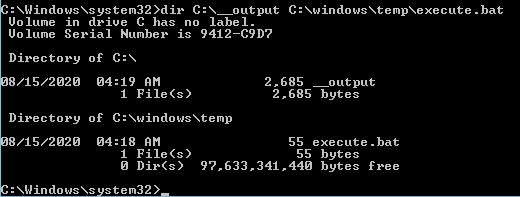
The file execute.bat will contain the full command executed:
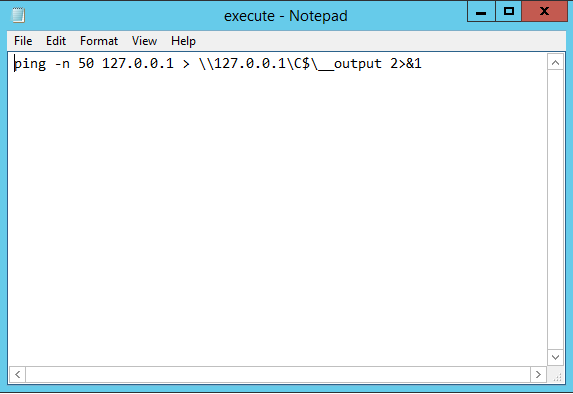
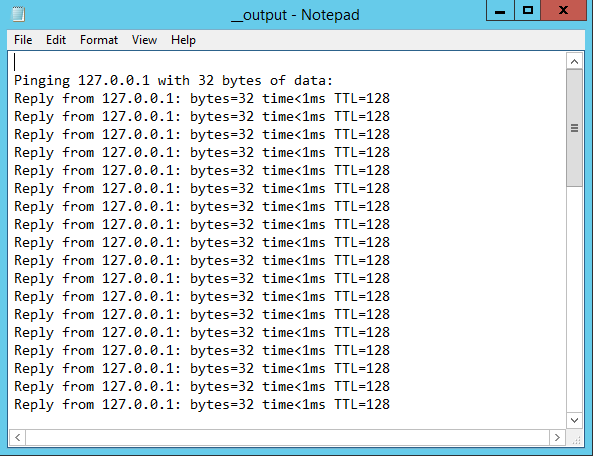
And the file __output will contain the results for execute.bat:
Keep in mind all of these name BTOBTO, __output and executable.bat could be changed easily. The following is a snippet from the source code for smbexec.py:
# TRUNCATED
OUTPUT_FILENAME = '__output'
BATCH_FILENAME = 'execute.bat'
SMBSERVER_DIR = '__tmp'
DUMMY_SHARE = 'TMP'
SERVICE_NAME = 'BTOBTO'
# TRUNCATED
The service name can also be changed using the switch -service-name.
Artifacts
The following is all artifacts generated by smbexec:
Windows Event Logs
| Event ID | Channel | Details |
|---|---|---|
| 4624 | Security | Successful login with the login type 3. You can find the source IP and username user. |
| 4634 | Security | Successful logoff with the same login id as the successful login above. This log along with the above log will show the semi-interactive shell session time. |
| 4672 | Security | Special privileges assigned to new logon. The logon ID is the same as the one in the event 4624. |
| 7045 | System | A new service will be created that contains the attacker command in the binPath field. By default the service name is BTOBTO. This event contains the most important data: 1. Malicious Service name 2. The command executed. 3. The user that executed this command (You can find the user SID in the XML view in System > Security > UserID). 4. The time when the command executed (Event time). |
| 7009 | System | A timeout was reached with the same service name. |
File System ($MFT)
| Path | Details |
|---|---|
| C:\windows\temp\execute.bat | The command to be executed will be written here. The default file name is execute.bat. |
| C:\__output | This file contains the command results. The default file name is __output. |
Rhaegal Rules
private SMBExecServiceCreated
{
metadata:
author: "AbdulRhman Alfaifi"
reference: "internal research"
creationDate: "10/08/2020"
score: 200
description: "Detected remote execution tool smbexec.py"
Channel: "System"
include:
EventID: "7045"
returns:
- "Data.ServiceName"
- "Data.ImagePath"
- "Security.UserID"
- "Channel"
}
private SMBExecServiceTimeout
{
metadata:
author: "AbdulRhman Alfaifi"
reference: "internal research"
creationDate: "10/08/2020"
score: 200
description: "Detected remote execution tool smbexec.py"
Channel: "System"
include:
EventID: "7009"
returns:
- "Data.param2"
- "Channel"
}
public SMBExecDetected
{
metadata:
author: "AbdulRhman Alfaifi"
reference: "internal research"
creationDate: "10/08/2020"
score: 200
description: "Detected remote execution tool smbexec.py"
include:
rule:
- "SMBExecServiceCreated"
- "SMBExecServiceTimeout"
if:
within: 500
}
public SMBExecSessionStarted
{
metadata:
author: "AbdulRhman Alfaifi"
reference: "internal research"
creationDate: "10/08/2020"
score: 200
description: "Detected remote execution tool smbexec.py"
Channel: "System"
include:
EventID: "7045"
Data.ImagePath: "*echo cd*"
returns:
- "Data.ServiceName"
- "Data.ImagePath"
- "Security.UserID"
- "Channel"
}
The above is two Rhaegal rules:
- SMBExecDetected: This is a public rule that contains two private rules (SMBEexecServiceCreated and SMBExecServiceTimeout) which will detect all command executed even if the default names changed.
- SMBExecSessionStart: This is a single public rule that detects echo cd in the service image path value which indicates the beginning of the session.
These rules has been added to Rhaegal Github repo, You can try this rule along with the other rules from HERE.