Impacket Remote Execution Tools: atexec.py
This is the first blog post in a series of blogs that look into Impacket remote execution tools. On these blog posts we will analyze these tools, understand how they work and how to detect them using multiple artifacts. In addition we will write Rhaegal and YARA rules to help with the detection.
What is Impacket ?
Here is description from Impacket GitHub
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets and for some protocols (e.g. SMB1-3 and MSRPC) the protocol implementation itself. Packets can be constructed from scratch, as well as parsed from raw data, and the object oriented API makes it simple to work with deep hierarchies of protocols. The library provides a set of tools as examples of what can be done within the context of this library.
Lab Environment
This lab environment does not have any kind of additional monitoring or logging (the default config) to simulate worst case scenario. The following table lists the lab environment specifications:
| Hostname | IP | Operating System | Role |
|---|---|---|---|
| LAB-DC01 | 10.10.10.2 | Microsoft Windows Server 2012 R2 Standard | Domain Controller (lab.com) |
| LAB-EXCH01 | 10.10.10.3 | Microsoft Windows Server 2012 R2 Standard | Exchange Server (Target Machine) |
| PC | 10.10.10.138 | Kali | Attacking Machine |
The tools used for monitoring are:
- EventLogMinitor : is a tool written by me to read Windows Event Logs in real time. You can find the tool Here
- Process Monitor : used to detect other system events (file system events,network events,registry events,etc).
- Process Explorer : better visualization for process tree.
- Rhaegal : A tool written by me to detect malicious/suspicious logs from windows event logs using Rhaegal rules. You can find Rhaegal Here
Analysis
I will remotely execute the command whoami on the server LAB-EXCH01 from the IP 10.10.10.138 with the username adam.wally. The user adam.wally is a local admin on the server LAB-EXCH01. After executing the following command:
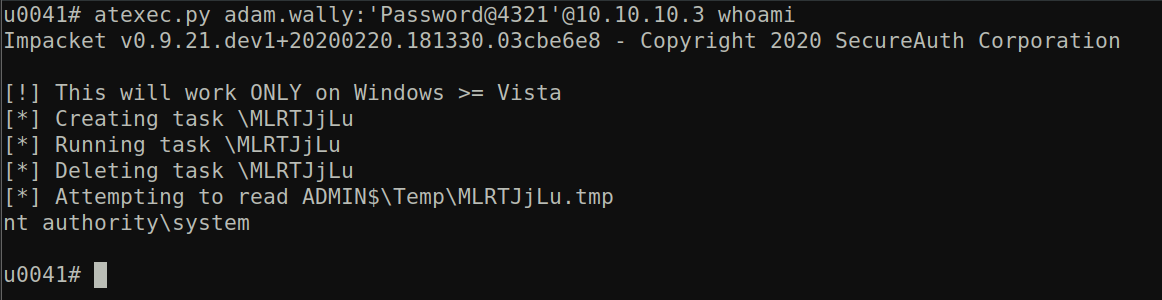
We can see the tool creates windows task named MLRTJjLu trigger the task manually then delete it. The name of the task is randomized on every execution of the tool. We can take a look at the source code of the tool to see how this name is generated. Here is the code responsible for the task name generation:
import string
# ...
tmpName = ''.join([random.choice(string.ascii_letters) for _ in range(8)])
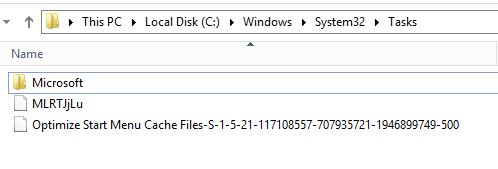
The task name (tmpName) is random capital and small letters with a length of eight characters. The tool deletes the tasks after triggering the task manually, However some times the tool crashes before deleting the task. In this case we can find the task with the same random name above in the path C:\Windows\System32\Tasks.
All windows tasks are in XML format. Let’s take a look at the file:
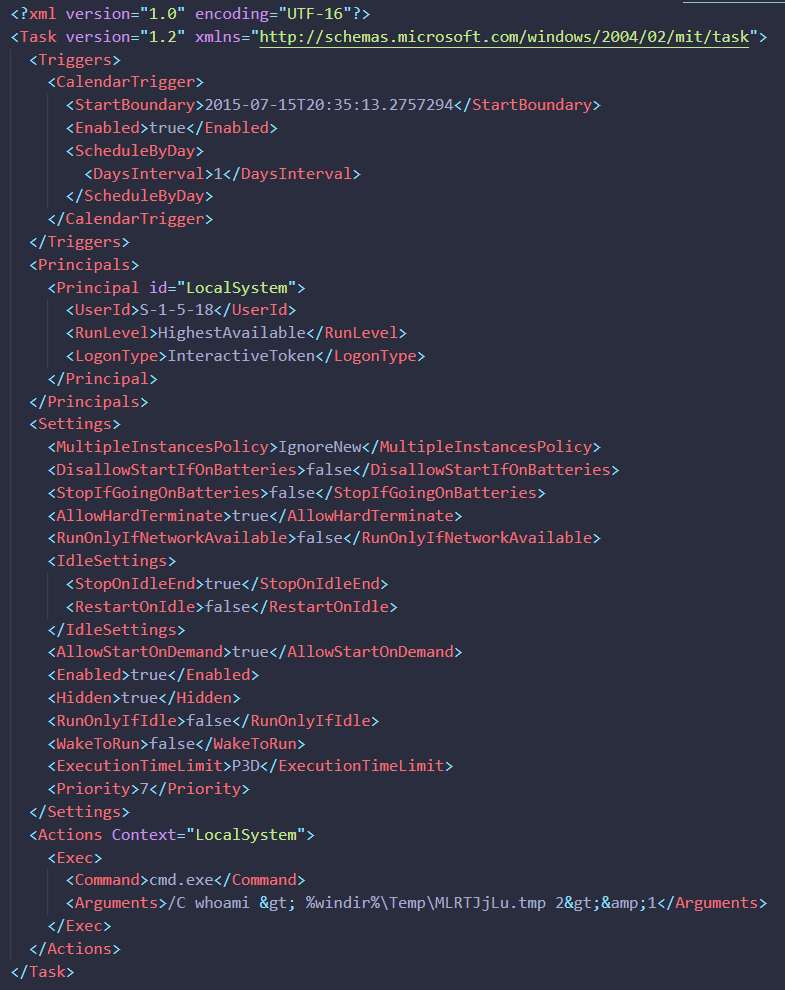
We can see that the command we executed is available in the Action section.
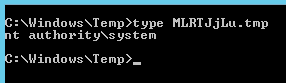
The way atexec works does not allow interactive sessions, So how does it retrieve the command results ? simply it writes the results to a file named the same as the task name + .tmp to the temp directory (C:\windows\temp\). For example:
- Task Name : MLRTJjLu
- Results File : C:\windows\temp\MLRTJjLu.tmp
atexec also deletes command results from the temp directory after retrieving the file. However sometimes atexec crashes or the tool get stopped before finishing which results in the file not getting deleted.
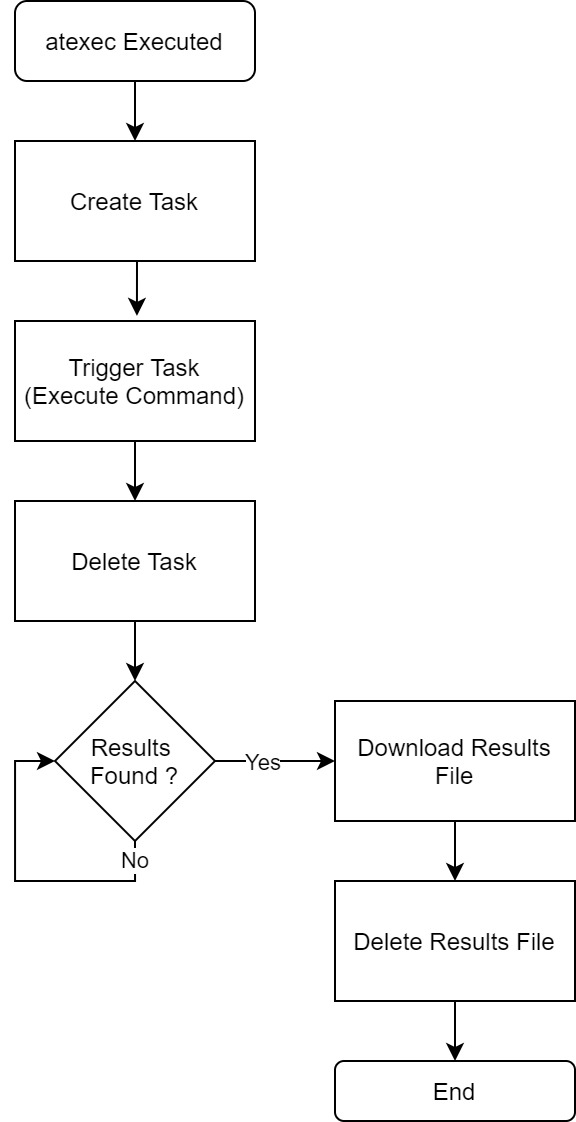
The below diagram summarizes how atexec works:
Artifacts
The following is all artifacts generated by atexec:
Windows Event Logs
| Event ID | Channel | Details |
|---|---|---|
| 106 | Microsoft-Windows-TaskScheduler/Operational | New Task Creation. in this log you will find the task name and the username used to create the task. |
| 110 | Microsoft-Windows-TaskScheduler/Operational | Task triggered by user. After the task creation the task will be trigger manually. |
| 141 | Microsoft-Windows-TaskScheduler/Operational | Task Deleted. Delete the task after execution |
| 4624 | Security | Logon type 3 and NTLM protocol used - 2 logins one for the task creation and the second is for retrieving the results. |
| 4634 | Security | Logoff with the same login ID as the login event above. The time between the first login and it’s logoff indicates the time taken to run the command. |
| 1015 | Microsoft-Windows-SMBServer/Security | Contains the attacking IP |
File System ($MFT)
| Path | Details |
|---|---|
| C:\windows\temp\[a-zA-Z]{8}.tmp | The results of the executed command. Normally this file gets deleted, However some times it does not. |
| C:\windows\system32\tasks\[a-zA-Z]{8} | This is the task that contains the command to be executed. Normally this file gets deleted, However some times it does not. |
Rhaegal Rules
private ATExecTaskCreated
{
metadata:
author: "AbdulRhman Alfaifi"
reference: "internal research"
creationDate: "03/07/2020"
score: 70
description: "Detected remote execution tool atexec.py"
Channel: "Microsoft-Windows-TaskScheduler/Operational"
include:
EventID: "106"
modifiers:
- Data.TaskName $rex \\[a-zA-Z]{8}
returns:
- "Data.TaskName"
- "Data.UserContext"
- "Channel"
}
private ATExecTaskDeleted
{
metadata:
author: "AbdulRhman Alfaifi"
reference: "internal research"
creationDate: "03/07/2020"
score: 70
description: "Detected remote execution tool atexec.py"
Channel: "Microsoft-Windows-TaskScheduler/Operational"
include:
EventID: "141"
modifiers:
- Data.TaskName $rex \\[a-zA-Z]{8}
returns:
- "Data.TaskName"
- "Data.UserContext"
- "Channel"
}
public ATExecDetected
{
metadata:
author: "AbdulRhman Alfaifi"
reference: "internal research"
creationDate: "03/07/2020"
score: 70
description: "Detected remote execution tool atexec.py"
include:
rule:
- "ATExecTaskDeleted"
- "ATExecTaskCreated"
if:
within: 100
}
The above rule is a private Rhaegal rule that detects task creation and deletion within 100 milliseconds with the task name that matches the task name generated by atexec (8 capital and small letters).